A WAF, or web application firewall, is a virtual security appliance, cloud service designed to protect organizations at the application level by filtering, monitoring and analyzing hypertext transfer protocol (HTTP) and hypertext transfer protocol secure (HTTPS) traffic between the web applications and the internet.
与Radware的Uri Dorot一起观看此Radware Minute剧集,了解什么是Web应用防火墙、拥有防火墙的重要意义、工作原理以及选择防火墙时应注意的事项。
WAF可保护Web应用免受跨站伪造、服务器端请求伪造、文件包含漏洞和SQL注入等攻击。此外,它还可为应用和网站防范漏洞、漏洞利用和零日攻击。对应用的攻击是导致数据泄露的主要原因——而数据泄露就是攻击者获取您宝贵数据的途径。通过采用适当的WAF,您可以成功拦截一系列旨在通过破坏系统以渗漏数据的攻击。
When a WAF is deployed in front of a web application, a protective shield is placed between the web application and the internet that monitors all the traffic between the application and the end user(s). A WAF protects the web apps by filtering, monitoring, and blocking any malicious HTTP/S traffic traveling to the web application, and also prevents any unauthorized data from leaving the application by adhering to a set of policies that help determine what traffic is malicious and what traffic is safe. Just as a proxy server acts as an intermediary to protect the identity of a client, in a traditional deployment, a WAF operates in similar fashion but in the reverse—called a reverse proxy—acting as an intermediary that protects the web app server from a potentially malicious client.
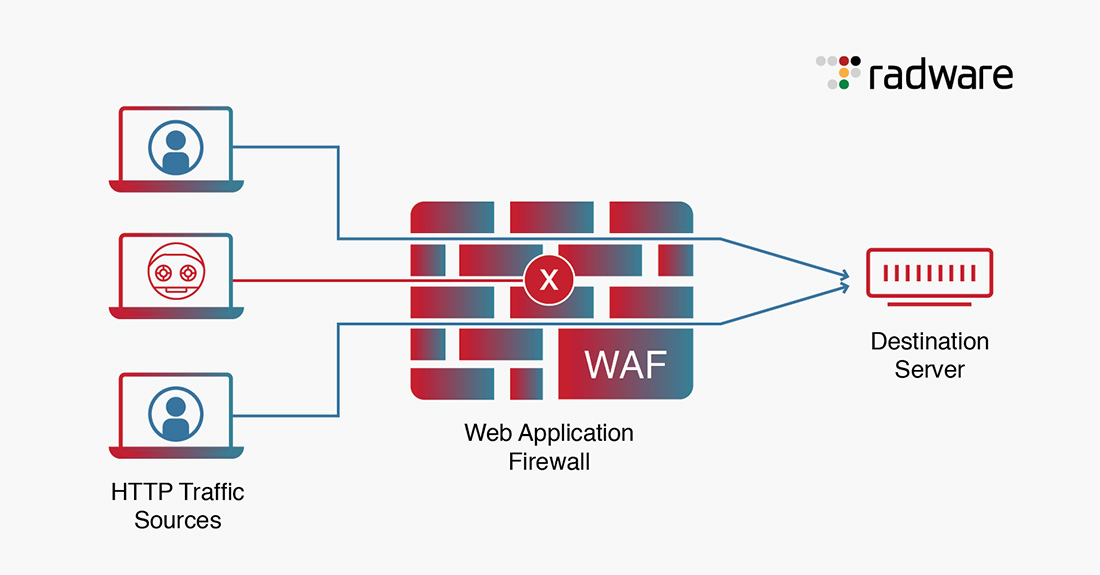
There are three approaches to security that WAFs typically take:
Whitelisting– An “allow list” that uses machine learning and behavior modeling algorithms to define what traffic the WAF lets through. It then blocks the rest.
Blacklisting– A “block list” based on up-to-date signatures against known vulnerabilities that defines what traffic the WAF denies. The rest is accepted.
Hybrid Approach– The WAF relies on a combination of both positive and negative security models—a combination of allow and block lists that determines what gets through.
The main difference between a firewall and a web application firewall is that a firewall is usually associated with protection of only the network and transport layers (layers 3 and 4). However, a web application firewall provides protection to layer 7.
WAF可以通过多种方式实施,每种方式都有其特有的优点与劣势。WAF分为三种类型:
- 网络端WAF通常基于硬件。由于其安装于本地,因此可以最大限度地减少延迟,但同时需要实体设备的存储和维护。
- 软件端WAF的管理者是以安全即服务形式提供WAF的服务提供商
云端WAF可提供一种经济实惠且易于实施的选择;其通常提供一站式安装,和更改DNS以重定向流量一样简单。由于用户按月或按年为安全即服务付费,云端WAF的前期成本也很低。云端WAF还可以提供持续更新的解决方案,以抵御最新的安全威胁,无需用户承担任何额外的工作或成本。云端WAF的弊端是用户要将责任移交给第三方。
理想情况下,WAF应当可以采用内联部署(让该解决方案充当“中间方”),或者作为基于API的路径外(OOP)服务部署。基于API的OOP部署具有若干特有的优势,使其能够针对多云环境进行优化。从而让应用请求可以不间断地直接从客户端发送至应用服务器。其优点包括减少延迟、无需流量重定向、增加正常运行时间和提供跨越各种环境的全面保护。
理想情况下,WAF应结合主动和被动安全模型以提供全面保护,其中包括能够缓解已知的Web应用攻击,例如非法访问、隐藏在CDN背后的攻击、API篡改和攻击、上述HTTP/S泛洪和暴力破解攻击等。此外,这种组合还可防范未知攻击和漏洞,例如零日攻击。
Web应用防火墙还应利用基于行为的机器学习算法,以实时创建和优化安全政策,从而提供全面保护,同时最大限度地减少或彻底消除误报。此功能还会在新应用添加至网络时自动检测和保护新应用。
WAF应包括的其他主要功能为:
- 核心功能应包括基于地理封锁、IP组、拦截列表、允许列表、白名单和黑名单筛选网络流量
- API发现和保护:提供对各种形式的API滥用和操纵的可见性、对策实施和风险缓解(无论是针对内部部署环境还是云托管环境)
- Built-in DDoS protection to stop the aforementioned application-layer DDoS attacks
- The ability to integrate with bot management solutions to detect and integrate sophisticated, human-like bots
- 数据泄露预防机制:自动屏蔽敏感用户数据,如个人可识别信息(PII)
由于采用敏捷开发方法、向云中迁移、对基于Web的软件或SaaS应用的使用增加以及员工队伍远程办公,许多企业在应用层面面临越来越大的安全风险。采用WAF使各企业能够化解针对Web应用和应用编程接口(API)的攻击。
虽然WAF无法为企业防范所有数字威胁,但其确实可以解决针对应用层面的威胁,包括OWASP 10大应用漏洞。其中包括:
- 跨站脚本攻击(XSS):一种代码注入攻击,在这种攻击中,攻击者会在合法网站中插入恶意代码。然后,该代码在用户的Web浏览器中作为受感染的脚本启动,使攻击者能够窃取敏感信息或冒充用户。
- Application-Layer DDoS Attacks: A volumetric DoS or DDoS assault focused at the application layer. Common examples include HTTP/S floods, SSL attacks, slow and slow attacks, and Brute Force assaults.
- SQL注入:SQL注入攻击类似于XSS,在这种攻击中,攻击者利用已知漏洞将恶意SQL语句注入应用。这转而让黑客得以提取、更改或删除信息。
- 零日攻击:零日攻击是指黑客在软件开发人员发布补丁之前利用未知的安全漏洞或软件缺陷。
According to Quadrant Knowledge Solutions’ research, the following are key market drivers for WAF:
- WAF providers wanting to improve their offerings are integrating their products with security information and event management (SIEM) systems, application security testing (AST) and web access management (WAM).
- Vendors are providing WAF solutions that are based on a positive security model and use a machine learning algorithm to analyze HTTP requests.
- Thanks to the increase in IoT devices, it’s likely organizations will invest in WAF solutions to comply with data privacy norms, including IoT-specific features such as device fingerprinting and protocol validation.
- Enterprises are seeking enhanced threat intelligence, extended WAF protection and a variety of out-of-the box integrations.
- There’s a focus on new detection methods to prevent web attacks and minimize false positives.
Radware's Products & Serveces