In today’s evolving threat landscape, it’s important to understand the way your cybersecurity solutions work—and the way they work with other solutions. This is especially true when it comes to web application firewall (WAF) and network firewall solutions, which stand guard against advanced cybercriminal activity including sophisticated and innovative cyberattacks. Knowing the right way to protect your organization from threats to your web applications and network can be the difference between staying secure and dealing with the aftermath of an attack.
A web application firewall (WAF) is a hardware appliance, virtual appliance or cloud-based service that resides in front of web-facing applications to detect and protect against a variety of malicious attacks. A WAF is focused on Layer 7 web application traffic (HTTP/S) and protects applications in internet-facing zones of the network.
A WAF can use many techniques to understand whether traffic should be allowed to pass through to an application or should be blocked. Some of those techniques are part of a negative security model that is based on block lists of known signatures, and some belong to a positive security model that is based on allow lists driven by machine-learning and behavioral-based algorithms. Most WAFs rely on negative security models only. Some more advanced WAF use a combination of a positive security model with a negative security model.
Lastly, WAFs are transitioning from standalone tools into fully-integrated web application and API protection (WAAP) offerings that include a suite of capabilities, including protecting APIs, bot management and mitigation capabilities, application Layer 7 DDoS protection, client-side protection and more.
Learn more in our detailed guide to WAF security
Network firewalls protect against unauthorized access to a computer network. Network firewalls prevent unauthorized access by creating and separating a secure zone from a less secure zone. They use configuration and access control policies to control communications between the two zones. Network firewalls usually operate at OSI Layer 3 and 4 and focus on network protocols such Domain Name System (DNS), File Transfer Protocol (FTP), Simple Mail Transfer Protocol (SMTP), Secure Shell (SSH) and Telnet.
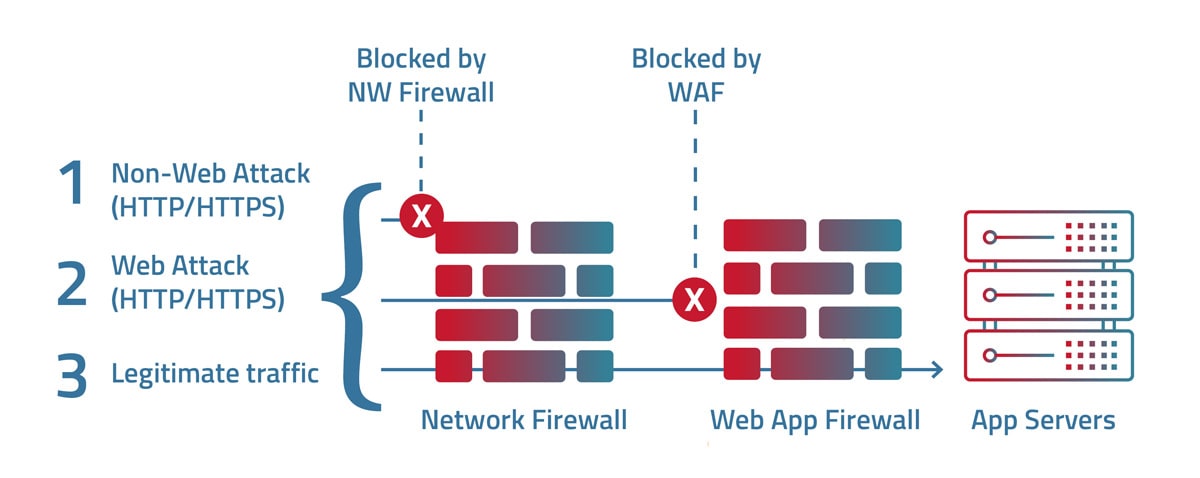
A network firewall and a web application firewall (WAF) are both security solutions that help protect against cyberattacks, although they differ in the way they work, the internet layer and protocols they monitor and the types of attacks they are designed to protect against. WAFs secure web traffic by filtering and monitoring HTTP traffic (OSI layer 7) between web applications and end-users. They employ a different set of security policies to detect and prevent attacks such as injection, cross-site scripting, server-side request forgeries, and other web application attacks. In contrast, network firewalls monitor and control Network and Transport layers traffic (OSI Layers 3 and 4) based on pre-defined security policies to ensure unauthorized traffic is denied entry.
While both solutions play crucial roles in cybersecurity, their main differences lie in their features and functionalities. A WAF plays a vital role in securing web applications and can defend against web-related attacks. Typically, a WAF is deployed in front of web servers to protect against complex HTTP- and HTTPS-based attacks that may target application vulnerabilities. On the other hand, a network firewall predominantly complements network security by preventing unauthorized access to networks through its intrusion-prevention features.
Not properly securing web applications can have severe implications for organizations. When a web application is compromised, hackers can gain access to sensitive information, modify application functionalities or shut down systems, compromising critical business data. Therefore, deploying both a WAF and a network firewall is essential for the complete protection of web applications. WAFs protect against web app-specific threats by filtering malicious HTTP and HTTPS traffic, while network firewalls secure web applications' back-end infrastructure.
Network Traffic vs. Application Traffic
Network traffic and application traffic are two concepts in cybersecurity that are critical to understand. Network traffic refers to the flow of data packets between devices in a network, while application traffic refers to the flow of data between applications on the same or different hosts. Unauthorized access to this traffic represents a significant threat to organizations. It occurs when a cybercriminal gains access to an application or network without authorization. For application traffic, such access can occur if a person exploits vulnerabilities in an application. In contrast, network attacks target unauthorized access and aim to access network resources, compromising the system and causing damage or disruption.
Mitigating these threats is obviously important. Intrusion prevention systems and firewalls are deployed to prevent network attacks. Meanwhile, web application firewalls (WAFs) inspect and filter HTTP traffic to an application, blocking malicious traffic that could cause harm. It's important to note that both network and application traffic are potential targets in a cyberattack, emphasizing the significance of robust cybersecurity measures. Having suitable tools in place, such as WAFs, firewalls and IDPSs, is essential to protect against unauthorized access and mitigate vulnerabilities, ensuring crucial data stays safe from cyberattacks.
Layer 7 vs Layer 4 & 3 Protection
Layer 7 protection and Layer 3 and 4 protections are both critical components of network security protection mechanisms. Layer 7 protection refers to an application-level protection mechanism that focuses on observing the application's traffic, recognizing patterns, and rejecting malicious traffic that doesn't conform to the traffic's typical application. In contrast, Layer 3 and 4 protections refer to network-level protection that is based on standard TCP/IP and UDP protocol suites, focusing on controlling the flow of traffic based on the source and destination IP addresses and ports. The key difference between the two methods is that Layer 7 protection focuses on rejecting anything that is not explicitly allowed by application protocols. Layers 3 and 4, on the other hand, focus on restricting traffic that does not match pre-defined rules based on IP addresses, ports or protocols.
Unauthorized Access Vs. Web Attacks
Unauthorized access and web attacks are two distinct cybersecurity concepts. Unauthorized access refers to unauthorized entry into a system or network without permission, often with the intention to steal, modify or destroy information. Examples of unauthorized access include:
- Password cracking
- Use of stolen credential
- Physical theft of devices or hard drives
On the other hand, web attacks focus on exploiting vulnerabilities in web applications, aiming to access web applications' sensitive data or services via security loopholes. Examples of web attacks include:
- SQL injection
- Cross-site scripting (XSS)
- Server-side request forgery (SSRF)
The key difference between the two is the target and type of attacks. While unauthorized access focuses on gaining access to a system or network infrastructure, web attacks concentrate on the application layer. In both cases the aim of the attackers is to steal data or impact the performance of the application and the organization network. But the methods and type of attacks are different – while attacks on the network layer we will see malicious actors trying to infect the organization network with viruses, worms, malware to take control over different functionalities and endpoint devices and servers, or turn “recruit” them to a botnet, in attacks on the web application layer, we will see the use of injections and all sorts of http manipulations to try to get to the application database, take over end-user accounts, or manipulate the web application performance and functionality. Understanding the difference between unauthorized access and web attacks is crucial to implementing effective cybersecurity measures to prevent their occurrence.
网络防火墙和WAF可抵御不同类型的威胁并且相辅相成。WAF依靠网络防火墙来抵御网络第3层和第4层的攻击。
Next-generation firewalls (NGFW) add additional capabilities, including antivirus, anti-malware, intrusion prevention, URL filtering, and certain application security capabilities to their network firewall functionality.
然而,NGFW的用户仍然需要WAF/WAAP来提供更全面的应用保护,此外还需要保护已发布和未列出的API,以及僵尸程序管理/风险缓解功能。
比较表:WAF与网络防火墙
| |
WAF |
IPS |
| 侧重领域 |
Web applications – OSI layer 7 (HTTP/S) |
Network protocols at layer 3 and 4 of OSI model (Network and Transport layers) |
| 功能 |
保护面向互联网的区域中面向Web的应用 |
保护内部网络。将网络分隔为安全区域和不太安全的区域,并防止对安全区域进行未经授权的访问。 |
| 能力 |
针对XSS、CSRF、API安全、BOT保护、API发现的Web应用保护 |
保护DNS、FTP、SMTP、SSH和Telnet。NGFW增添了防病毒、反恶意软件和IPS功能以及一些应用安全性。 |